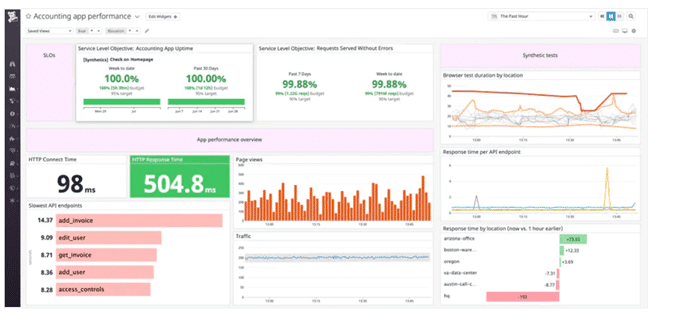
Synthetic monitoring enables you to improve the end-user experience by proactively verifying that important transactions can be completed and key endpoints accessed.
It simulates a user view of your application and provides high-level performance information that can quickly drive your investigation.
It helps you ensure uptime, identify problems, track application performance, and manage your SLAs and SLOs.
You can continuously simulate HTTP, TCP or SSL connections to verify not only that your applications are up and responding to requests, but also that conditions you define, such as response time, HTTP response code, header, up to SSL certificate expiration, are met.
Browser testing provides end-to-end visibility into every step of your application’s key workflows, such as signing up for an account or adding items to a shopping cart.
It becomes possible to simulate traffic from custom locations that are important to your business, such as call centers, warehouses, offices or where your key customers are located.
Teams can be alerted to what is happening with internal applications before your users encounter problems.
Source: Datadog.