Most cybersecurity tools are designed to help identify, alert and in some cases, prevent a particular type of malicious activity.
Today’s technologies send alerts and can even prevent specific types of attacks, but the burden remains on the organization to determine whether that alert is meaningful in a broader context such as: the overall posture and whether that alert fits into a larger chain of malicious activity or actual attack.
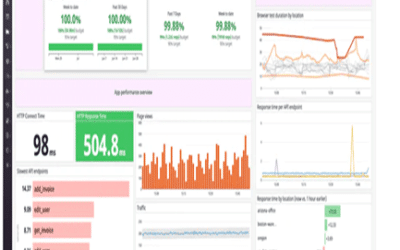
Centralizing logs is the critical first step to gaining visibility into a multi-layered security environment.
Download a free copy of 4 easy ways to centralize logs to improve security posture with information on:
- The importance of end-to-end visibility to improve your security posture
- How four common data sources can protect your organization
- How to use data sources to focus security investigations.
Source: Splunk